10 Simple Techniques For Managed It Services For Law Firms
Wiki Article
Top Guidelines Of It Services Melbourne
Table of ContentsHow It Services Melbourne can Save You Time, Stress, and Money.The Best Strategy To Use For It Services MelbourneManaged It Services for BeginnersSome Known Factual Statements About It Service Melbourne
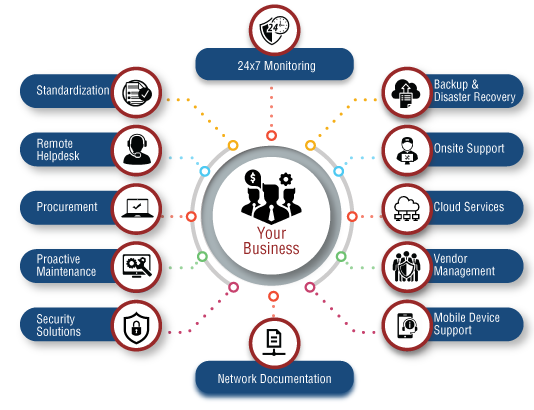
As foresaid, IT sustain offers end-to-end managed IT solutions, that include these generally: An IT facilities has a number of laptop computers, workstations, printers, web servers and equipment systems. A tiny damages or breakdown might finish up in a great loss, which can be of crucial data or information. This happening eventually influence on the company's returns and continuity.These policies have multi-factor authentication, stopping out of the state logins and also several various other ones in a wonderful role. This is remarkably for the firms that permit workers to utilize their very own phones for performing jobs. This bring-your-own-device (BYOD) is not every common, however still exists. The support supplying firms place their team to secure that information and also properties from hackers or misuse.
It ensures that just safe gadgets will be able to execute from another location, as they would can protecting the sensitive data of the business. It refers to the on-demand accessibility of computer system sources, including information storage space and computer power. This occurring does not call for any kind of direct active administration by the customer.
As its advantages are remarkable, an increasing number of companies have actually started changing to the cloud for holding their data. managed it services. For keeping their confidential information about customers and their customer experience (CX) secure, it features some extraordinary safety and security functions. The tech assistance group handles it well in 2 methods: Guaranteeing setting up and also managing the cloud system for hosting a number of requisite applications, data monitoring, IT support and downtime, Supplying the complete protection to what comes under the managed IT solutions from cyber offenders.
Not known Details About Managed It Services

Something failed. Wait a minute and attempt once again Try once more.
Services are significantly moving their visit this site right here IT infrastructures into the cloud. Many venture companies now run in multi-cloud settings or make use of hybrid on-premises as well as cloud-based IT designs.
Excitement About It Services Melbourne
Includes testing data healing remedies to guarantee that they are trusted as well as efficient in the event of an information loss or corruption. IT sustain is essential for services that count greatly on their information, such as those in the health care and money markets.Work environment technology alters quickly as well as gets a lot more intricate by the year. Whereas the mass of work-related computing when happened within the office wall surfaces and inside a secure border, today's distributed labor force conducts organization from homes, coffee shops, cars and trucks essentially anywhere with net access. Supporting as well as securing the myriad tools and also gain access to points workers now count on to stay productive has actually developed a whole lot even more job for IT groups that typically are already spread also thin.
Organizations look to taken care of companies (MSPs) for a variety of factors, however a lot of typically, they are utilized by organizations without inner IT group or those that want to use their internal IT professionals to concentrate on specific initiatives as opposed to operational duties for taking care of innovation. MSPs offer a vast variety of services from the basics such as assistance desk assistance and also keeping IT equipment and also solutions working right as much as providing the complete suite of IT abilities, consisting of cyber security, net connection, application support, data backups, and also catastrophe recovery.

Some Of Managed It Services Melbourne
Handled IT solutions are far from one-size-fits-all, so partnering with an MSP who recognizes your business as well as is proactively bought helping you fulfill your goals is important.Prospective risks outside the network are stopped, making certain that a company's delicate information remains within. Organizations can go even more by defining added inner boundaries within their network, which can offer improved safety and security and also gain access to control. Accessibility control defines the individuals or groups as well as the gadgets that have accessibility to network applications and also systems therefore rejecting unsanctioned accessibility, and also perhaps threats.
A susceptability is a bent instance in a software navigate to this website program system as well as a make use of is an assault that leverages that vulnerability to gain control of that visit this website system. When a manipulate is revealed, there is usually a window of possibility for attackers to manipulate that vulnerability before the security patch is used.
Sandboxing is a cybersecurity technique where you run code or open data in a risk-free, separated atmosphere on a host maker that imitates end-user operating environments. Sandboxing observes the documents or code as they are opened and looks for harmful actions to stop dangers from jumping on the network. Malware in data such as PDF, Microsoft Word, Excel and Power, Point can be safely spotted and also blocked before the files reach an unsuspecting end user.
Report this wiki page